腾讯安全发布勒索病毒报告:目标是锁定政企用户,显著增强破坏力
本月微软补丁日提前公开了六个缺陷,其中两个Windows特权提升缺陷CVE-2019-0797和CVE-2019-0808被外国平安研究员发现野外行使,微软紧急修复了这两个Win32k提权0day破绽。本月微软补丁日提前公开了六个缺陷,其中两个Windows特权提升缺陷CVE-2019-0797和CVE-2019-0808被外国平安研究员发现野外行使,微软紧急修复了这两个Win32k提权0day破绽。
CVE-2019-0797是一个win32k由于未记录的系统挪用了驱动程序中的竞争条件造成的缺陷NtDCompositionDiscardFrame和NtDCompositionDestroyConnection它们之间缺乏准确的同步。黑客需要登录系统,并通过操作特殊应用程序行使缺陷进行攻击。乐成行使缺陷可以让黑客在核心模式下操作任何代码,黑客可以完全控制受影响的系统。
这是除了CVE-2018-8589和CVE-2018-8611之外,统一APT组织SandCat使用的第三种行使竞争条件0day缺陷攻击。缺陷的影响从Windows 8到Windows 10 1703 64位的所有操作系统。

CVE-2019-0808上周宣布在野外行使的一枚0day缺陷,缺陷的行使方式与前者相似,乐成行使它可以让黑客在核心模式下运行随机代码。
攻击者和Chrome浏览器0day破绽CVE-2019-5786一起发动破绽行使攻击。CVE-2019-5786辅助攻击者逃跑Chrome平安沙箱后,再行使CVE-2019-0808执行恶意代码其恶意代码的权限。
此外, 本月还一次性宣布了三次Windows DHCP客户端远程执行代码缺陷(CVE-2019-0697,CVE-2019-0698,CVE-2019-0726),影响Windows 10 1803- Windows 10 1809的所有系统都可以在没有用户交互的情况下行使,乐成行使后可以在客户端计算机上操作任何代码。缺陷威胁水平高,建议优先修复。
破绽号:CVE-2019-0808
曝光时间:2019-03-13
破绽风险水平:主要
破绽曝光水平:已公开
软件及版本受影响:
Windows 7 for 32-bit Systems Service Pack 1
Windows 7 for 32-bit Systems Service Pack 1
Windows 7 for x64-based Systems Service Pack 1
Windows 7 for x64-based Systems Service Pack 1
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for Itanium-Based Systems Service Pack 2
Windows Server 2008 for Itanium-Based Systems Service Pack 2
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 R2 for Itanium-Based Systems Service Pack 1
Windows Server 2008 R2 for Itanium-Based Systems Service Pack 1
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
破绽号:CVE-2019-0797
曝光时间:2019-03-13
破绽风险水平:主要
破绽曝光水平:已公开
软件及版本受影响:
Windows 10 for 32-bit Systems
Windows 10 for x64-based Systems
人生中最猛烈的黑客攻击是什么?
Windows 10 Version 1607 for 32-bit Systems
Windows 10 Version 1607 for x64-based Systems
Windows 10 Version 1703 for 32-bit Systems
Windows 10 Version 1703 for x64-based Systems
Windows 10 Version 1709 for 32-bit Systems
Windows 10 Version 1709 for 64-based Systems
Windows 10 Version 1709 for ARM64-based Systems
Windows 10 Version 1803 for 32-bit Systems
Windows 10 Version 1803 for ARM64-based Systems
Windows 10 Version 1803 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 8.1 for 32-bit systems
Windows 8.1 for 32-bit systems
Windows 8.1 for x64-based systems
Windows 8.1 for x64-based systems
Windows RT 8.1
Windows Server 2012
Windows Server 2012
Windows Server 2012 (Server Core installation)
Windows Server 2012 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 R2
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2 (Server Core installation)
Windows Server 2016
Windows Server 2016 (Server Core installation)
Windows Server 2019
Windows Server 2019 (Server Core installation)
Windows Server,version 1709 (Server Core Installation)
Windows Server,version 1803 (Server Core Installation)
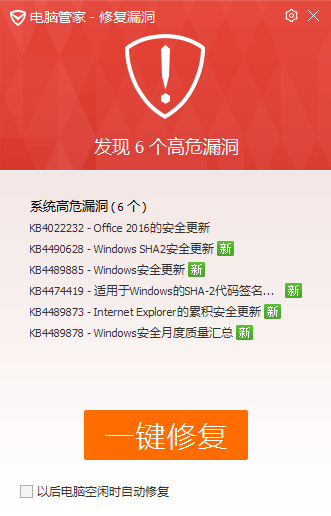
现在腾讯电脑管家已经第一次推出了上述缺陷补丁。为了防止被黑客攻击,建议大家及时修复缺陷,珍惜个人隐私和安全。
微软安全通知链接:
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-0797;
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-0808;
参考链接:
https://securelist.com/cve-2019-0797-zero-day-vulnerability/89885/
Black Hat Asia 腾讯安全第一次披露Chakra JIT发动机漏洞攻击面